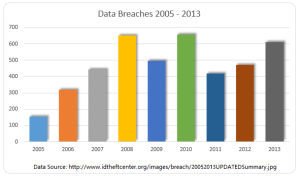
September 18th, 2017 by Elma Jane
Smart Security for Smart Businesses:
Safe-T for SMB streamlines the PCI process while providing the layered security needed to protect card data
EMV – Fraud protection at the point of sale
EMV chip technology keeps the consumer’s card in their hand. It also helps protect the business from card-present fraud related chargebacks.
Encryption – Protection of payment card data in-transit
Safe-T scrambles cardholder data using advanced encryption technology, so data is protected at the point of entry, and throughout the authorization process.
Tokenization – Token ID protection of stored payment card data
Safe-T returns a token ID or an alias, consisting of a random sequence of numbers to the point-of-sale so the actual card number is never stored. Token IDs can be used for follow up transactions (i.e. recurring payments, voids, etc.).
Reduced PCI – Protection from complex PCI compliance
Maintaining PCI Compliance can be intimidating – second only, perhaps, to completing your taxes. Safe-T eases this process for customers by reducing the number of PCI Self-Assessment questions by more than 60% from 80 questions to 31.
Financial Reimbursement – Financial protection from a card data breach
Recovering from a card data breach can be costly for a small business. Safe-T offers Card Data Breach Reimbursement to financially protect your customer’s business in the event of a card data breach – regardless of the type of card data breach.
For Electronic Payment Set up with this feature call now! 888-996-2273
Posted in Best Practices for Merchants Tagged with: card data, card present, chargebacks, chip, data, data breach, EMV, encryption, fraud, payment, PCI, point of sale, Security, tokenization

June 28th, 2016 by Elma Jane
Financial Cost – on average, it costs a small business between $36,0000 and $50,000 in the event of a data breach. From PCI examination to liability costs and POS upgrades. The many costs of a data breach add up.
Notification Cost – if your business falls victim to a data breach, it is your moral and sometimes legal (depending on the state in which your business operates) obligation to notify your customers of the breach.
Reputation Cost – data breach lessens your credibility and trust with your customers. This can have a long-term affect on your business.
Time Cost – as a small business owner, your focus is on the daily operations of your business. In the event of a data breach, your focus will be shifted entirely to clearing up the issue.
The cost of a data breach is more than financial and can often have a lasting negative impact on your business.
The quickest and easiest way to protect your business is to prevent fraud from happening. At National Transaction, we give importance to your security. For your electronic payments needs give us a call at 888-996-2273.
Posted in Best Practices for Merchants Tagged with: customers, data breach, electronic payments, financial, fraud, PCI, POS, Security
May 6th, 2016 by Elma Jane
A data breach is any instance in which secure data information has been released or stolen intentionally or unintentionally. The organization that exposed or lost your information will notify you. The steps you should take depend on the type of information that was lost or stolen. In general, you may choose to do one or more of the following:
- Monitor all bank and other accounts for suspicious activity.
- Change all passwords, PINs, or user names associated with compromised accounts.
- Order a copy of your credit report.
- Place a fraud alert or credit freeze on your credit file.
Posted in Best Practices for Merchants, Credit Card Security, Travel Agency Agents Tagged with: accounts, bank, credit, data, data breach, fraud

March 23rd, 2016 by Elma Jane
A data breach can occur from inside a business just as much as it can externally. The one common element between both is “Opportunity.” It doesn’t matter whether a business is a multi-national corporation or a small single-location.
Attacks from criminals can range in sophistication. While the sophistication of some attacks may be low, experts note that criminals continue to evolve their techniques and now they are becoming more sophisticated than ever.
While large corporations may have millions of customer records, they also maintain the resources to protect their sensitive information from the average criminal. It may take weeks, months, or even years for a criminal to penetrate the defenses of one large corporation. This is why attacks on small business are becoming so attractive to criminals.
It all goes back to the “Opportunity.” The average small business lacks the resources to properly protect their business from the variety of attacks at the disposal of criminals. Or worse, they may believe their business is of no interest to criminals. The fact is, they are less secure than larger businesses. These are all issues for the average small business owner, and more importantly, their customers.
So what can a small business do to protect themselves from the growing threat of a data compromise?
- Background checks on employees.
- Have someone monitor the network activity.
- Protect business with proper network security protocols.
- Protect your payment’s environment by using a layered approach that includes EMV, encryption and tokenization to help prevent sensitive payment card data from being stolen.
These are all fairly simple and inexpensive ways for businesses to help protect themselves and their customers from being a victim of a costly data compromise.
Posted in Best Practices for Merchants, Credit Card Security, Travel Agency Agents Tagged with: card, customer, data, data breach, EMV, encryption, payment, Security, tokenization

February 2nd, 2016 by Elma Jane
Businesses continue to struggle with the prohibited storage of unencrypted customer payment data. The Payment Card Industry Data Security Standard (PCI DSS), merchants are instructed that, Protection methods are critical components of cardholder data protection in PCI DSS Requirement.
PCI DSS applies to every company that stores, processes or transmits cardholder information. Regardless of the size or type of business you operate, the number of credit card transactions you process annually or the method you use to do so, you must be PCI compliant.
Data breach is not a limited, one-time occurrence. This is why PCI compliance is required across all systems used by merchants.
Encryption and Tokenization is a strong combination to protect cardholder at all points in the transaction lifecycle; in use, in transit and at rest.
National Transaction’s security solutions provide layers of protection, when used in combination with EMV and PCI-DSS compliance.
Encryption is ideally suited for any businesses that processes card transactions in a face to face or card present environment. From the moment a payment card is swiped or inserted at a terminal featuring a hardware-based, tamper resistant security module, encryption protects the card data from fraudsters as it travels across various systems and networks until it is decrypted at secure data center.
Tokenization can be used in card not present environments (travel merchants) such as e-commerce or mail order/telephone order (MOTO), or in conjunction with encryption in card present environments. Tokens can reside on your POS/PMS or within your e-commerce infrastructure at rest and can be used to make adjustments, add new charges, make reservations, perform recurring transactions, or perform other transactions in use. Tokenization protects card data when it’s in use and at rest. It converts or replaces cardholder data with a unique token ID to be used for subsequent transactions.
The sooner businesses implement encryption and tokenization the sooner stored unencrypted data will become a thing of the past.
Posted in Best Practices for Merchants, Travel Agency Agents Tagged with: card, card data, card present, cardholder, compliance, credit card, customer, data, data breach, data security, e-commerce, EMV, encryption, Mail Order/Telephone Order, merchants, moto, payment, Payment Card Industry, PCI-DSS, POS, secure data, Security, terminal, tokenization, tokens, travel, travel merchants

December 14th, 2015 by Elma Jane
Reality of data theft means that a breach can sometimes have two or three aftershock effects years down the line.
Eighty five percent of American consumers admitted that if significant personal consequences present themselves after their information is compromised as part of a breach, they would have no problem seeking a new place to spend their money.
In particular, 67 percent said that they would cut ties with the victimized brand if money was actually removed from their checking accounts, 62 percent said so if their credit cards were charged for fraudulent purchases, 57 percent said the same if their personal information was released and 54 percent would look elsewhere if their credit scores were affected.
It’s been two years since major retail attacks made data breach a household word, vice president of enterprise data security firm said.
As it becomes easier for customers to switch their preferred brands, data breaches events can be too devastating for some merchants.
http://www.pymnts.com/news/2015/been-breached-say-bye-bye-to-customer-loyalty/
Posted in Best Practices for Merchants Tagged with: Breach, credit, data breach, data security, merchants
October 31st, 2014 by Elma Jane
It is a given that damage to a retailer’s reputation is one of the biggest negative outcomes from a big data breach. However, research said that customer service or the lack thereof, is a bigger turn-off for consumers than a data breach, and by a wide margin.
In April 2014 research, 75 percent of almost 800 survey respondents said poor customer service would have the greatest impact on a company’s reputation. Some type of environmental incident was the second most determining factor in reputational damage, at 33 percent, with a data breach coming in third at 30 percent.
Data breach management
According to the 2014 survey, businesses can do themselves the most good in the wake of breaches by explaining the potential risks or harms of the compromises, disclose the facts of the incidents and tell the unvarnished truth. Sixty-seven percent of respondents believe explaining the risks/harms to them of data breaches is the best way companies can improve communications, followed by fact disclosures and not sugar coating the message.
When asked what businesses could do to prevent customers from ending relationships with them following breaches, 41 percent said offering free identity theft protection and credit monitoring services would help out.
Consumer attitudes contradictions
When consumers are victimized by data breaches, their fears of also becoming victims of identity theft increase. Following a data breach, that fear nearly doubles. Furthermore, following breaches, victimized consumers in the survey said that their identities were at risk for years or forever.
But curiously enough, when consumers received data breach notifications that they may have been victimized, 32 percent of respondents ignored the notifications and took no action and only 18 percent followed the advice provided in the notifications.
Nevertheless, most consumers seem to recognize what types of data are the most sensitive and would cause the most stress and financial damage if compromised. Respondents said the compromise of Social Security numbers would lead to the most potential damage, followed by password/PIN and bankcard account information.
If you are out of business because of financial impact the data breached cost you. How good is your service? Losing even a single customer can be very costly. It’s critical for companies to turn a complaint into a positive for the customer and for the company moving forward.
Posted in Best Practices for Merchants Tagged with: bankcard account, consumers, credit monitoring services, customer service, data breach, password/PIN
October 15th, 2014 by Elma Jane
Another day, another corporate data breach. Business owners are now aware that cyber criminals are becoming increasingly smart and sophisticated in their hacking methods, and they can target just about anyone. But smaller companies that think, It can’t happen, or they are too small for hackers to notice, may be setting themselves up for a devastating data breach.
Large corporations typically have a lot more money and resources to invest in IT security, whereas small to medium businesses do not have the IT staffing, resources, money or know-how to put effective security measures into place to combat security vulnerabilities.
If a small business owner is responsible for security practices, it’s going to fall to the lower end of the priority list. The business will have less protections in place and hackers recognize that. Criminals are looking for unlocked doors.
Recent research found that more than half of all small and midsize businesses have been hacked at some point, and nearly three-quarters weren’t able to restore all the lost data. The two most common methods of attack are phishing, gathering sensitive information by masquerading as a trusted website and watering holes. Installing malware on commonly used websites of a target group. These tactics, grant cyber criminals access to the information that leads to identity theft and stolen credit card information.
A credit card breach is fairly easy to recognize once customers of a certain company all begin reporting fraudulent charges. But by that point, a breach has already done a significant amount of damage, not just to the consumers but to the company they trusted to protect their data.
A computer that appears to have been tampered with.If you turned off your computer when you left work and it’s on or has windows and programs running when you return, someone may have been trying to steal important information. This is an especially likely scenario with internal data theft, such as the AT&T breach. Keeping your machines password-protected and encrypting any sensitive data can prevent unauthorized individuals from accessing the information.
Locked-out accounts. If you’ve ever been locked out of your email or social media accounts, you know it’s usually because you typed the wrong login credentials one too many times. If you receive a lock-out message the first time you try to access an account (and you know you’ve typed your password correctly), you might have been hacked. This can mean that someone is attempting to brute force an account, or that an account has already been compromised and the password changed.
Unusually slow Internet or computers. This could be a sign of a compromised machine that is sending out lots of traffic, or that malware or a virus is on the machine. You should also look for pop-up ads (especially if you have an activated blocker) or websites that don’t load properly.
In all of these instances, minor inconveniences that most people might ignore if the problem seems to resolve itself could be signs of a much more serious problem. Both experts advised keeping your antivirus software, firewalls and device operating systems up-to-date, and always remaining alert for any suspicious activity.
Posted in Best Practices for Merchants Tagged with: consumers, credit card breach, credit card information, customers, data, data breach, device, Security, website
September 23rd, 2014 by Elma Jane
Home Depot, US retail chain says that 56 million payment cards are at risk following a malware-laden cyber-attack on eftpos tills across its stores in the US and Canada.
The investigation into a possible breach began on September 2nd,Tuesday morning, immediately after Home Depot received reports from its banking partners and law enforcement that criminals may have breached its systems.
According to Home Depot’s security partners, the malware had not been seen previously in other attacks.
Criminals used unique, custom-built malware to evade detection. The cyber-attack is estimated to have put payment card information at risk for approximately 56 million unique payment cards, after lurking in the company’s eftpos tills for four months between April and September.
While the breach has been seen as a further proof-point in the US push to adopt Chip and PIN at the point-of-sale, the fact that the outbreak also hit the home improvement chain’s Canadian stores, where the EMV standard has been implemented, leaves pause for thought. Nonetheless, the retailer has committed to installing 85,000 PIN pads at its US outlets, well ahead of the national 2015 deadline.
Home Depot has set aside $65 million to cover the cost to investigate the data breach, provide credit monitoring services to its customers, increase call center staffing, and pay legal and professional services. Approximately $27 million of the projected outlay will be covered by the company’s insurance.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Point of Sale Tagged with: banking partners, Breach, call center, card information, cards, Chip and PIN, credit monitoring, credit monitoring services, customers, cyber-attack, data breach, EMV, EMV standard, Malware, payment, payment card information, payment cards, PIN pads, point of sale, risk
February 3rd, 2014 by Elma Jane
The migration to cards that use chips instead of magnetic strips, known as EMV technology, is well underway in the U.S. No government regulation is needed to make it happen. But the EMV migration and the Target breach are different things. It’s true that EMV chip cards can prevent criminals from producing counterfeit cards using stolen account numbers. But EMV doesn’t stop criminals using stolen cards online. So innovators are deploying new technologies to deter other forms of fraud.
Headline-grabbing events inevitably lead to calls for new laws. But in the case of our nation’s electronic payments systems, new government mandates would stifle marketplace innovations that hold great promise for providing consumer benefits and reducing criminal activities.
Financial institutions compete for customers by providing consumer protections even beyond requirements of current law. Many retailers also offer customers speedy transactions, such as “sign and go” and “swipe and go” for small transactions, while the payments industry ensures consumers still have zero liability. These protections and flexibility are why U.S. consumers are going cashless and carry more than one billion debit and credit cards. More than 70% of retail purchases are made with electronic payments, and our member companies process more than $4 trillion in electronic payments each year.
Fraud accounts for fewer than six cents of every $100 spent on payments systems – a fraction of a tenth of a percent. U.S. companies have made significant financial and technological investments, building sophisticated fraud tools that insulate consumers from liability. To build on this, Congress should foster greater international law enforcement cooperation to fight cybercrime, particularly in countries that harbor crime rings, and replace 46 divergent state breach notification laws with a uniform national standard.
The private sector is best positioned to address the constantly shifting tactics of criminals, and it is doing so without government mandates. Do Americans really want the government in charge of the security and monitoring of our payments?
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Security, Electronic Payments, EMV EuroPay MasterCard Visa, Financial Services, Visa MasterCard American Express Tagged with: counterfeit cards, cybercrime, data breach, debit and credit cards, electronic payment systems, electronic payments, emv chip cards, emv technology, fraud, liability, magnetic strips, migration, online, security and monitoring of our payments, small transactions